Before understanding PBKDF2. What is it?
In cryptography, PBKDF1 and PBKDF2 (Password-Based Key Derivation Function 1 and 2) are key derivation functions with a sliding computational cost, used to reduce vulnerability to brute-force attacks
Modern Hashing Algorithms
Nowadays most industries using modern hashing algorithms such as Bcrypt, PBKDF2, and Argon2id. These hashing algorithms have high computational costs, which means that the time taken to hash a single password is comparatively higher than legacy hashing algorithms.
Key Derivation Process
The PBKDF2 key derivation function has 5 input parameters.
DK = PBKDF2(Password, Salt, PRF, c, dkLen)The output of the PBKDF2 function is the Derived Key. (In our case DK is the hashed value)
- Password:- The master password from which the derived key is generated. (In our case, this is the password that needs to be hashed)
2. Salt:- Sequence of bits known as cryptographic salt.
3. PRF:- Pseudo-Random Function is the basic building block of PBKDF2 in constructing the key derivation function.
PBKDF2 applies the PRF many times to the password. This means that an attacker who tries to crack the password needs to apply the function many times.
4. c:- The number of iterations that need to be performed.
The choice of no.of iterations can be varied according to the environmental conditions. Iteration count can be increased to increase the security.
Note:- Increasing the iteration count will not be a significant burden for legitimate parties, but it would be a significant burden for opponent parties.
5. dkLen:- Generated derived key bit length.
The derived key (hashed value) length can be specified according to the requirements.
Industry Applications of PBKDF2 Password Hashing
- Microsoft Windows Data Protection API (DPAPI)
- Keeper (for password hashing)
- LastPass (for password hashing)
- 1Password (for password hashing)
- Enpass (for password hashing)
- Dashlane (for password hashing)
- Bitwarden (for password hashing)
- Standard Notes (for password hashing)
- Mac OS X Mountain Lion (for user passwords)
- Apple’s iOS mobile operating system (for protecting user passcodes and passwords)
- WinZip (AES Encryption Scheme)
- Django (web framework, as of release 1.4)
Resource:
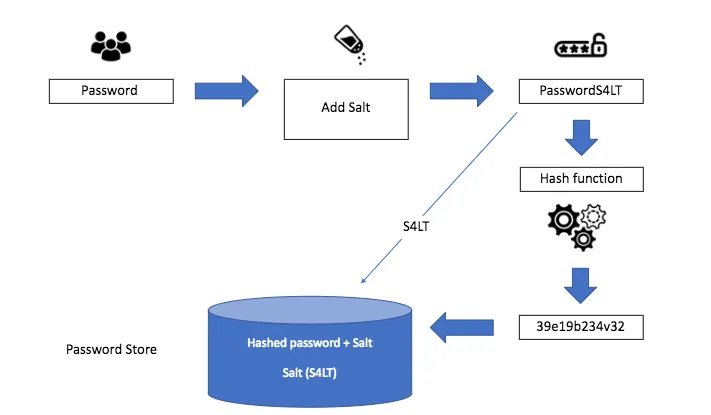
Salt (cryptography)
In cryptography, a salt is random data fed as an additional input to a one-way function that hashes data, a password or passphrase.[1] Salting helps defend against attacks that use precomputed tables (e.g. rainbow tables), by vastly growing the size of table needed for a successful attack.[2][3][4] It also helps protect passwords that occur multiple times in a database, as a new salt is used for each password instance.[5] Additionally, salting does not place any burden on users.